Overview:
F5 DDoS Hybrid Defender provides next-generation cloud and on-premises distributed denial-of-service (DDoS) defenses to ensure real-time protections against volumetric DDoS threats; dynamic network and applications attacks; and threats hiding within encrypted traffic.
DDoS attacks remain a significant concern, and are a leading cause of business service outages facing organizations today. Such attacks threaten businesses of all sizes, and are often used as a smoke screen for more sophisticated and dangerous hacks or theft. DDoS attacks have evolved to be multi-layered and complex—it’s no longer about just attacking the network: the application layer is directly in the crosshairs. How quickly you discover and stop attacks is critical to keeping your business applications operational.
Why F5 DDoS Hybrid Defender?
- Complete coverage in a single offering with combined network and application DDoS defense, SSL/TLS decryption, behavioral analysis, and cloud scrubbing.
- Sub-second attack detection with geo-tracking, intelligent signaling, and hardware assist— inline or in out-of-band mode.
- In-depth and real-time attack visibility for more effective decisions with 3000+ L3–L4 metrics, detailed logging, actionable reports, and intelligence sharing.
- Proactive bot defense that discovers malicious bot activity in advance of attacks.
4 truths about today’s DDoS attacks.
- Many DDoS attacks aim to render a service unavailable by overwhelming it using multiple sources. All connections look ok.
- It’s only getting easier to launch an attack (people can get paid for participating in an attack, IoT devices can become attack bots, etc.)
- Attacks are more sophisticated and targeted: For example, multi-vector attacks leveraging Transport Layer Security (TLS) connections and malware planted in IoT and other devices to create botnets.
- It’s essential to defend against multiple attack types that target the weakest link, whether that’s your network, WAN bandwidth, or applications.
How traditional solutions fall short
Multiple vulnerability vectors have spawned multiple point solutions.
Network layer (or flood) attacks are best handled at the edge of the network, protecting the assets that are behind the firewall. But the usual defense of black holing or rate limiting can cripple the connections of legitimate users.
Application layer attacks, which are more sophisticated and targeted, require SSL decryption in front of app servers inside the network. Typical solutions are blind to SSL traffic and dependent on their placement in the network.
WAN bandwidth saturation shuts down your connection to the Internet. So any on-premises defense is useless against it.
Simply put, traditional point DDoS solutions are only partially effective because they focus solely on one type of attack.
A new depth of defense
DDoS Hybrid Defender is the only multi-layered defense that protects against blended network attacks andsophisticated application attacks, while enabling full SSL decryption, anti-bot capabilities, and advanced detection methods—all in one appliance.
It also delivers the highest performance with line rate capabilities and without impacting legitimate traffic.
Point by point—DDoS Hybrid Defender vs. the competition
In contrast with competing products, DDoS Hybrid Defender provides comprehensive protection for both the data center and the application. Here are a few reasons why it’s more effective than the competition:
Sophisticated attacks require a lot of processing. Other solutions don’t have the performance to simultaneously decrypt SSL, process traffic, and mitigate attacks in-line.
DDoS Hybrid Defender delivers a true multi-layered defense from a single box with a dual-mode appliance that supports both out-of-band processing and inline mitigation.
Identifies good vs. bad traffic using behavioral-based attack detection with the ability to sustain DDoS under very high connect rates and volume.
Enables a faster response to volumetric and blended attacks with a true, dedicated solution that stops attacks on your data center immediately and integrates with Silverline cloud services for sub-second off-loading. It also features unique layer 7 application coverage that even stops threats hidden behind DDoS attacks without impacting legitimate traffic.
Features:
Protection Against Mult-vector Attacks
Detect and protect against simultaneous attacks from layer 3 through layer 7.
Cloud-Based Volumetric Attack Protection
Integrated on-premises device with Silverline cloud-scrubbing service, protecting against WAN bandwidth saturation attacks.
Scalability
Protection against even the largest DDoS attacks at line rate.
Variety of Attack Detection Mechanisms
Sub-second attack detection, threshold based—packets per second (PPS), transactions per second (TPS), requests per second—and behavioral and signatures-based attack detection.
Traffic Baselining and Auto Configuration
Baseline the traffic to automatically size the configuration.
Variety of Attack Mitigation Mechanisms
SHUN, RTBH, BGP steer, and Silverline cloud-based services.
Variety of Deployment Mechanisms
Deployment options include inline (layer 2 and layer 3), out-of-band, TAP, and bump-in-wire.
Threat Intelligence
Immediate protection—at line rate—against known bad actors and sharing that intelligence between on-premises deployments and the cloud.
Simplified Configuration and Management
Manage all DDoS settings from a single screen and only see the information important to you. Simplify configuration workflows for DDoS profiles, IP intelligence, virtual servers, and log profile setup.
Visibility into Attacks via Analytics and Reporting
Get current attack details like impact on throughput, CPU, and memory. Event logs provide both historical and recent attack data and mitigation details. Customized reports let you pinpoint the data you’re most interested in.
Key Solution Benefits:
Stateful Security, Stateless Scale
F5 DDoS Hybrid Defender delivers the best of both stateful and stateless security. The stateful capabilities help to detect and defend against the broadest range of layer 4-7 attacks including SYN Flood, SSL/TLS protocol attacks, and application low-and-slow attacks. These stateful capabilities are executed with the performance and resiliency of a stateless solution, providing the best of both worlds: intelligent, stateful protection with the dependability and scale of a stateless solution.
Ultra-Resilient Hybrid Design
F5 DDoS Hybrid Defender integrates with the F5 Silverline DDoS Protection, a high performance cloud-scrubbing service. The hybrid combination delivers unmatched performance and resiliency to defend against the most intensive of attacks. The on-premises appliance serves as the primary defense under normal conditions. When needed, F5 DDoS Hybrid Defender redirects volumetric attack traffic to the Silverline cloud scrubbing centers. Expert F5 Security Operations Center (SOC) engineers analyze the attack and signaling detail, and implement mitigations to scrub network traffic, which prevents saturation of inbound pipes on-premises. Once attack traffic has subsided to normal levels, DDoS Hybrid Defender and Silverline DDoS Protection smoothly transition back to on-premises protection.
Operations Speed
F5 DDoS Hybrid Defender helps your SOC staff run with efficiency and intelligence: you won’t need a large staff to make a big impact. Self-tuning and automated, the solution deploys easily without the need for managed services. F5 DDoS Hybrid Defender learns optimal performance levels and automatically determines appropriate thresholds. You won’t waste staff time on continuous tuning and complicated traffic analysis, providing faster value than other solutions.
The dashboard provides your team with what they need to see, so they won’t waste time chasing down false positives. When action is required, your staff can take immediate mitigation actions with just a few clicks. Rapid, real-time updates show the mitigation results so that SOC staff can be assured the threat has been mitigated.
Self-Tuning and Automated Behavioral Defense
In addition to the standard security signatures, the solution creates dynamic signatures automatically—enabling faster and more accurate threat identification and blocking of evasive threats. These include low-and-slow and short, sporadic bursts of traffic that may go undetected. Security policy implementation is not a one-time procedure. F5 DDoS Hybrid Defender discovers and fingerprints new and unusual traffic patterns without human intervention, distinguishing and isolating potential malicious traffic from legitimate traffic almost instantaneously. Mitigation aggressiveness is based on sophisticated analysis of network and application stress. The aggressiveness of automated mitigations is determined using the current health of applications and networks. Real-time status is fed back to the mitigation engine, where mitigation signatures are automatically built, deployed, and analyzed for effectiveness. This reduces false positives and enables a “hands-off” automated protection cycle that continuously tunes and refines the precision of the mitigations as the attack continues or evolves—scaling mitigations up and down as needed.
F5 Security Intelligence
Information from all DDoS attacks discovered and mitigated by on-premises devices and F5 Silverline DDoS Protection can be automatically communicated to F5 SOCs for expert research and global threat analysis. This information, combined with F5’s global threat feeds, drives standard signature updates and security enhancements. Collectively, the trend analysis intelligence helps F5 safeguard against future threats.
Deploy Where You Need It Most
F5 DDoS Hybrid Defender eliminates common concerns with deployment, especially where network architectures are more complex. It offers an interface designed for the security professional, and a simplified “out-of-the-box” experience—with automatic sizing and configuration of DDoS protection features. Its flexible deployment options enable DDoS protection services to be easily deployed within the data center as a physical or virtual appliance, directly in the path of traffic or out of band for analysis of traffic behavior.
Deployment:
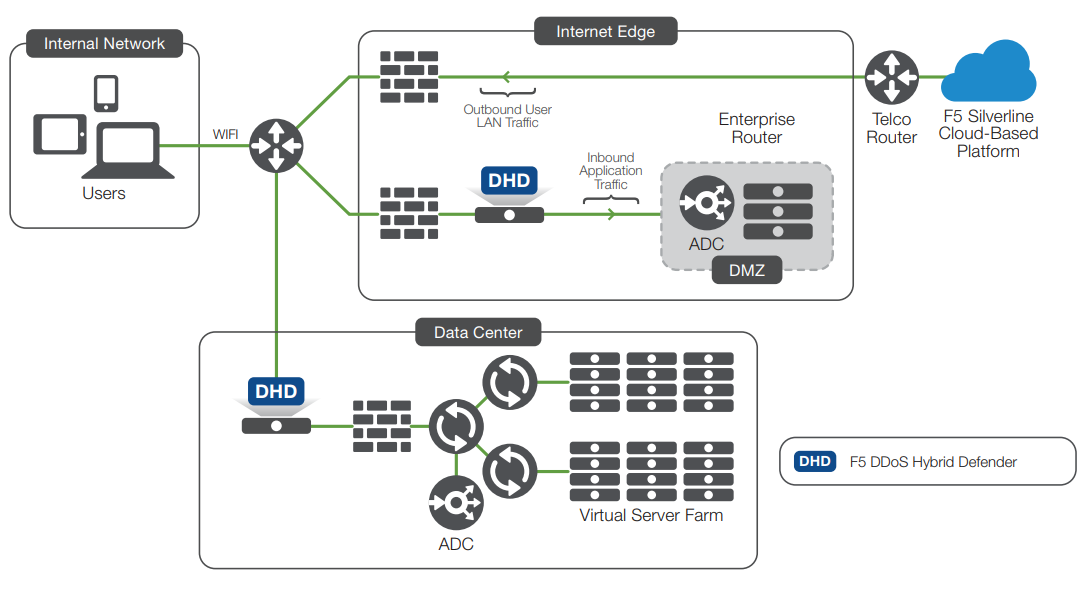
Specifications:
F5 DDoS Hybrid Defender protects the most complex infrastructures, enabling organizations to improve data center and application level security, protect customer data and access, and enhance overall security postures.
| Specifications |
| DDoS Mitigation |
All layer 3, 4, and 7 DoS/DDoS threats including flood/sweep with Src/Dst IP address awareness, UDP/DNS/HTTP/TCP/SIP/SYN/ ACK/RST/FIN using sub-second detection, network behavior analysis, 120+ DDoS vectors, application anomaly detection, dynamic filtering, protocol analysis, source tracking, control policies, and more. |
| DDoS AutoThresholding |
Automatically generated and adjusted for all DDoS network and application threshold values for TPS, PPS, and requests per second. |
| Comprehensive Bot Defense |
Proactive bot defense, captcha challenges, headless browser detection, bot categorizations identifying severity and good/bad bots, device fingerprinting. |
| IP Intelligence |
Bad actor information can be communicated across other DHD devices; F5 IP Intelligence licensed services provide global DDoS threat intelligence feeds. |
| DDoS Detection |
Out-of-band SPAN port, NetFlow monitoring. |
| SSL Inspection (Decryption) |
Advanced, purpose-built TLS stack. Hardware accelerated: Key exchange and bulk inspection; RC4, DES, 3DES, AES-CBC, AES-GCM, AES-GMAC, RSA, DSA, DH, ECDSA, ECDH, MD5, SHA, SHA2 ciphers. Keys protected by F5 BIG-IP Secure Vault. FIPS 140-2 Levels 1, 2 and 3 available. |
| Reporting and Forensics |
Dashboard summary, current attack and drill-down reporting, standard and customizable charts and graphs; blocked/passed traffic; app health, bot signatures; Top 10 threats/destination IPs/source IPs; sys mon; max # of attacks; IPs participating in attack. |
| Mitigation Techniques |
Rate limiting/blocking, connection limiting, source limiting, shunning/ blacklisting/whitelisting, BGP route injection and RTBH (source and destination), dynamic signature filtering. Volumetric/cloud scrubbing redirection: manual or automated. |
| Management |
REST; CLI, Web UI; RBAC management |
| Deployment Modes |
Asymmetric and symmetric flow support. Inline and Out-of-Path: L2 Bridged, L2 Virtual Wire, and L3. Out-of-Band: SPAN/Tap and Netflow. Form Factors: BIG-IP Appliance, Virtual Edition, network functions virtualization, VIPRION chassis. |
| Event Notifications |
SNMP, Syslog, email |
| Cloud Signaling |
BGP/BGP Flowspec route injection for manual or automated redirection to licensed F5 Silverline or third-party volumetric scrubbing solutions. REST API route activation with licensed F5 Silverline DDoS Protection cloudbased scrubbing. |
| High Performance (HA) |
Support HA active/passive |



