Overview:
The BIG-IP iSeries platform combines software and hardware innovations that balance the need for performance, scalability, and security. iSeries delivers unrivalled software-defined hardware performance, fast and easy programmability, and ecosystem-friendly orchestration. IT teams can offload SSL processing and deploy comprehensive application delivery and security services across data center and colocation infrastructure.
Speed and flexibility: obtain 2x price/performance
F5 TurboFlex optimization technology offloads specialized functions from the general CPU, resulting in up to 2x the price/performance of leading competitors.
Comprehensive security: protect critical apps and data
Innovations in the BIG-IP iSeries platform balance performance, scalability and security, enabling you to implement security services such as WAF, network firewall, firewalling and application access controls to protect your environment.
Compliance at scale: meet your regulatory requirements
BIG-IP iSeries is FIPS and Common Criteria certified, enabling you to comply with regulatory requirements and get the best protection for all of your application environments.
Lower total cost of ownership: make your IT budget go further
Reduce your total cost of ownership and infrastructure footprint by consolidating app delivery and security services on to a unified, high-performance platform.
Gain Agility with the Most Programmable Cloud-Ready ADC
F5’s next-generation, cloud-ready Application Delivery Controller (ADC) platform provides DevOps-like agility with the scale, security depth, and investment protection needed for both established and emerging apps. The new F5 BIG-IP iSeries appliances deliver quick and easy programmability, ecosystem-friendly orchestration, and record breaking, software-defined hardware performance. As a result, customers can accelerate private clouds and secure critical data at scale while lowering TCO and future proofing their application infrastructure.
Key Benefits
Obtain the lowest TCO
Reduce TCO and the infrastructure footprint by consolidating app and security services on to a unified, high-performance platform.
Protect critical data
Deliver the SSL capacity required to protect critical data—including offload of elliptical curve cryptography (ECC) processing to hardware—enabling forward secrecy scaling. Simplify operations and improve customer confidence with the fastest way to an SSL Labs A+ rating.
Secure applications
Deliver the most effective protection with integrated, one-pass, full stack (L3–L7 security, including an ICSA Certified firewall, highcapacity DDoS mitigation, contextual access management, and more.
Ensure the easiest deployment for cloud or container environments
Save time with the only simple, out-of-the-box native integration with leading private cloud, cloud interconnect colocation, and container environments.
Maximize investment protection
The iSeries’ software-defined hardware includes unique F5 TurboFlex FPGA technology that enables on-demand optimized performance for specific use cases such as DDoS protection or UDP traffic processing. Eliminate forklift upgrades and extend the lifecycle of app delivery hardware with software-upgradeable performance.
Maximize uptime
Ensure your critical infrastructure is built on reliable, carrier-grade hardware with hot-swappable components, redundant power supplies and fans, and always-on management integrated with a full baseboard management controller (BMC) with IPMI support.
Standardize Your App Delivery Services
BIG-IP ADC appliances can simplify your network and reduce total cost of ownership (TCO) by offloading servers, providing a consistent set of comprehensive application services, and consolidating devices, saving management, power, space, and cooling costs in the data center.
The massive performance and scalability of the BIG-IP platform reduces the number of ADCs needed to deliver even the most demanding applications. By offloading computationally intense processes, you can significantly reduce the number of application servers needed.
Intelligent Performance Where It Matters
Traditional performance measurements in terms of throughput don’t accurately represent the complex needs of delivering modern web applications. Connection capacity and L7 transactions per second are critical. For instance, ADCs must be able to process high levels of layer 4 and layer 7 connections and make application-layer decisions such as removing sensitive information or transforming application-specific payloads. BIG-IP appliances have the intelligence and performance to handle application layer decisions while securing your data and infrastructure.
The Advantages of F5 BIG-IP Hardware:
The BIG-IP iSeries platform perfectly blends software and hardware innovations that balance the need for performance, scalability, and agility. The F5 TMOS operating system provides total visibility, flexibility, and control across all application delivery services. With TMOS, organizations can intelligently adapt to the diverse and evolving requirements of applications and networks. Other unique or patented hardware and software innovations enable the BIG-IP iSeries platform to offer unmatched capabilities:
- F5 TurboFlex optimization technology: Field-programmable gate arrays (FPGAs), tightly integrated with CPUs, memory, TMOS, and software, provide specific packet-flow optimizations, L4 offload, support for private cloud tunneling protocols, and denial-ofservice (DoS) protection. These hardware optimizations not only improve performance but free CPU capacity for other app delivery and security tasks. Only BIG-IP iSeries appliances feature TurboFlex performance profiles—user-selectable, pre-packaged optimizations that provide different performance characteristics depending on the business need:
- L4 offload enables unsurpassed throughput and reduced loads on software.
- Unique per-virtual-IP/application SYN flood protection ensures that if one application is under attack, others are not affected. Only F5 ADCs implement hardware-based SYN cookies in L4 and full proxy L7 mode.
- More than 100 types of DoS attacks can be detected and mitigated in hardware, hugely increasing the attack size that can be absorbed compared to software-only implementations.
- Network virtualization and overlay protocol processing (such as VXLAN and NVGRE tunneling) increases traffic processing capacity.
- UDP traffic processing increases throughput and reduces both latency and jitter, improving VoIP or streaming media performance.
- Best-in-market SSL performance accelerates SSL/TLS adoption by offloading costly SSL processing and speed key exchange and bulk encryption. BIG-IP iSeries solutions include hardware acceleration of ECC ciphers, enabling forward secrecy. In addition, the ability to achieve an SSL Labs A+ rating with a few simple steps reduces SSL configuration complexity and errors.
- BIG-IP platforms offer maximum hardware compression, enabling cost-effective offloading of traffic compression processing to improve page load times and reduce bandwidth utilization.
- Enterprise class SSD (solid state drive) technology on select BIG-IP platforms improves performance and reliability, saves power, and reduces heat generation and noise.
- Efficiency features include 80 Plus Platinum certified power supplies as well as front-panel touchscreen LCD management, remote boot and multi-boot support, and USB support.
F5 ScaleN
F5 ScaleN technology enables organizations to scale performance, virtualize, or horizontally cluster multiple BIG-IP devices, creating an elastic Application Delivery Networking infrastructure that can efficiently adapt as needs change.
- On-demand scaling—Increase capacity and performance with on-demand scaling, simply adding more power to your existing infrastructure instead of adding devices. Some BIG-IP appliance models can be upgraded to the higher performance model within each series through on-demand software licensing, which enables organizations to support growth without new hardware.
- Operational scaling—Virtualize ADC services with a multi-tenant architecture that supports a variety of BIG-IP versions and product modules on a single device. F5 Virtual Clustered Multiprocessing (vCMP) technology enables select hardware platforms to run multiple BIG-IP guest instances. Each guest instance acts like a physical BIG-IP device, with a dedicated allocation of CPU, memory, and other resources. vCMP offers per-guest rate limiting for bandwidth, enabling different performance levels for each guest.
Further divide each vCMP guest using multi-tenant features such as partitions and route domains, which can isolate configuration and networks on a per-virtual-domain basis. Within each virtual domain, you can further isolate and secure configuration and policies, with a role-based access system for administrative control. When route domains/partitions are combined with vCMP guests, F5 provides the highest density multi-tenant virtualization solution, which can scale to thousands of virtual ADC (vADC) instances.
This ability to virtualize BIG-IP ADC services means service providers and enterprise users can isolate based on BIG-IP version, enabling departmental or project-based tenancy as well as performance guarantees, consolidated application delivery platform management, and increased utilization.
- Application scaling—Increase capacity by adding BIG-IP resources through an all-active approach, and scale beyond the traditional device pair to eliminate idle and costly standby resources. Application scaling achieves this through two forms of horizontal scale. One is Application Service Clustering, which focuses on application scalability and high availability. The other is Device Service Clustering, designed to efficiently and seamlessly scale BIG-IP application delivery services and sync application policies.
Application Service Clustering delivers sub-second failover and comprehensive connection mirroring for a highly available cluster of up to eight devices at the application layer, providing highly available multi-tenant deployments. Workloads can be moved across a cluster of devices or virtual instances without interrupting other services and can be scaled to meet business demand.
Device Service Clustering can synchronize full device configurations in an all-active deployment model, enabling consistent policy deployment and enforcement across devices—up to 32 active nodes. This ensures a consistent device configuration, with syncing of hardened firewall and access policies to simplify operations and reduce attack surfaces.
Gain Agility and Control in Private Clouds:
Enterprises are migrating to private clouds to achieve agility and speed time to market for applications while maintaining control. Regardless of the chosen cloud stack, typically only basic networking and app services like load balancing are provided. Advanced application delivery and security services are required to optimize and protect applications. Highly scalable BIG-IP platforms, with programmatic interfaces and service delivery templates, enable integration and automation with orchestration systems and deliver rightsized services aligned to specific app needs.
F5 solutions integrate with the leading private cloud technology stacks, including OpenStack, VMware, and Microsoft. For OpenStack, F5 provides native orchestration with Heat templates to automate the end-to-end deployment of advanced app and security services, reducing deployment times from days to minutes. Integration with VMware vRealize Orchestrator through the Blue Medora vRO plug-in reduces configuration time, enables selfservice of F5 application services by app owners, and automates complex, multi-step workflows. F5 iWorkflow enables integration of F5 devices with software-defined networking (SDN) orchestration systems providing a single point of contact between the orchestrator and F5 devices.
Two-tier architecture
For enterprises deploying a private cloud, a two-tier architecture provides an optimized design that takes best advantage of both hardware and software app delivery services. The first tier provides services such as L4 traffic management, distributed denial-of-service (DDoS) firewall, or SSL offloading, which are centralized and shared for all north-south traffic entering the network, enforcing consistent app policies. These services, which deal with high-volume traffic and incur heavy CPU loads, require high performance, scalability, and guaranteed service-level agreements (SLAs). Dedicated, purpose-built hardware such as BIG-IP iSeries appliances meet those requirements and, depending on the environment and app requirements, can be more cost efficient than commodity servers.
Tier 2—the tenant or app tier—includes emerging, cloud-native applications that can be hosted in containers or disaggregated into microservices. The apps require specific services addressing intra-app traffic (east-west traffic). Those services, which can include basic load balancing to web app firewall or web performance optimizations, can be delivered on a per-application basis through highly scalable, flexible software such as virtual editions of BIG-IP products. This two-tier architecture model, standardized on F5 application services, offers flexibility, a strategic point of control where proven app policies can be enforced, and complete visibility of all traffic, taking advantage of hardware where it’s needed and software agility near the app.
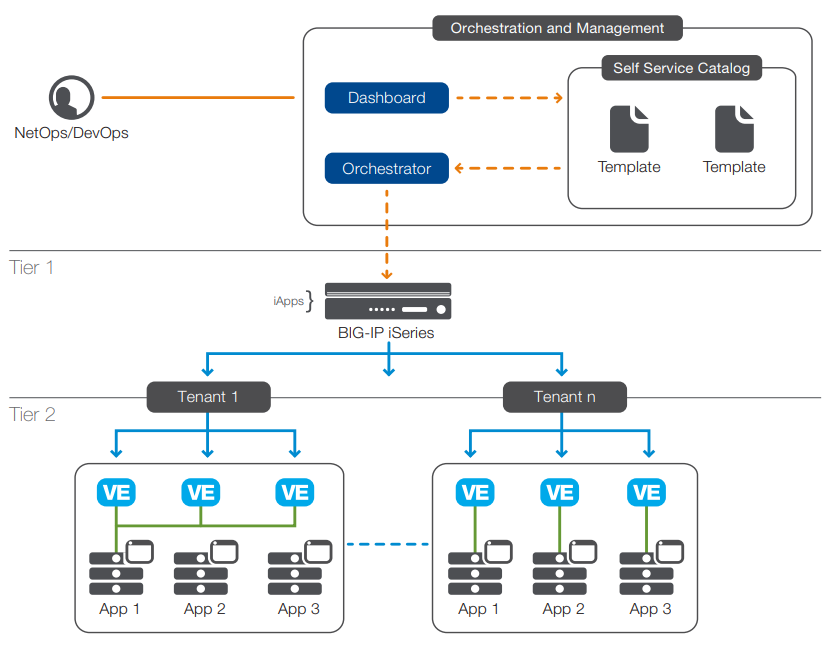
Figure 1: Orchestrated and automated deployment of app services in a two-tier private cloud architecture.
Consistent App Delivery and Security for Public Cloud
As more enterprise applications migrate to public cloud, it’s becoming more difficult to maintain network requirements and consistent application policies. In addition, many IT architects are unaware of the amount of public cloud apps deployed, the current configurations and services for those apps, and how to discover apps in flight. Organizations are turning to interconnection services at colocation providers for direct public cloud access; however, application delivery and security services across public cloud providers is disparate and varied, compared to on-premises and private cloud solutions.
F5 Application Connector is an add-on to the F5 BIG-IP platform, allowing services insertion for public cloud applications. It also acts as a cloud proxy instance for securely connecting public clouds to an organization’s application service infrastructure within cloud interconnects (colocations) or data centers. This enables the use of public cloud resources as part of an organization’s compute infrastructure. Application Connector also performs workload discovery within the Amazon Web Services (AWS) and Azure public cloud, and provides a secure connection back to interconnect services or data centers, allowing application services insertion on the BIG-IP platform.
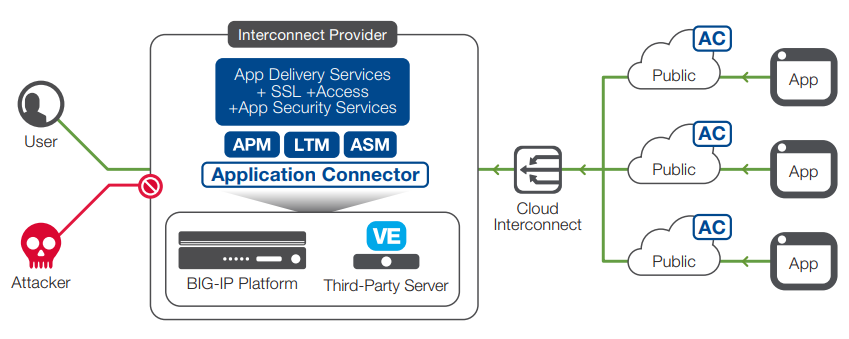
Figure 2: Application Connector helps you easily search and find public cloud-hosted workloads in AWS and Azure. Securely connect all public cloud apps, and insert app delivery and additional security services such as SSL. Provide consistency across app deployments, and securely maintain sensitive SSL keys from a central location.
Programmability
Enabling automation and orchestration is key to achieving the benefits of cloud and software-defined architectures and to scaling application services on demand. F5 platforms offers many ways to program the application services fabric and network, enabling organizations to automate deployment, react in real time to events, and easily integrate into orchestration systems. F5 iRules scripting has long provided granular traffic control and visibility, enabling customization, rapid response to code errors and security vulnerabilities, and support for new protocols. New F5 iRules LX lowers costs and speeds deployments by extending iRules to JavaScript developers and providing access to, and easier integration with, over 250,000 community Node.js packages. In addition, with F5 iApps templates, organizations can automate deployment and configuration of application services in minutes. F5 iControl® REST APIs and SDKs provide integration with leading open source and commercial orchestration systems, VMware, OpenStack clouds, and configuration management systems such as Puppet, Chef, and Ansible.
BIG-IQ Centralized Management
F5 BIG-IQ Centralized Management is F5’s management and orchestration platform. It provides a central point of control for F5 physical and virtual devices and the app delivery and security services that run on them. BIG-IQ Centralized Management is available both as a virtual edition and an F5 appliance. It simplifies management, helps ensure compliance, and gives you the visibility and reporting you need to troubleshoot and respond to issues and security attacks.
BIG-IQ Centralized Management manages policies, licenses, SSL certificates, images, and configurations for F5 devices and the following BIG-IP software modules:
- BIG-IP Local Traffic Manager (LTM)
- BIG-IP Application Security Manager (ASM)
- BIG-IP Advanced Firewall Manager (AFM)
- BIG-IP Access Policy Manager (APM)
- F5 Secure Web Gateway Services
- BIG-IP DNS
- F5 WebSafe and F5 MobileSafe (monitoring only)
BIG-IQ Centralized Management supports BIG-IP appliances, VIPRION chassis/blades, and BIG-IP virtual editions (VE), whether they are running locally or in the cloud. It is ideal for organizations that require central management of F5 devices and modules, license management of BIG-IP VEs, or central reporting and alerting on application availability, performance, and security.
Simplified and enhanced diagnostics and troubleshooting
BIG-IP iSeries appliances include a baseboard management controller (BMC) and support for the Intelligent Platform Management Interface (IPMI) protocol. With the BMC and Always-On Management (AOM) firmware, F5 customers can have deeper access to internal sensor data for system monitoring, including multiple thermal, airflow, and voltage readings. Out-of-band alerts for hardware-level problems are possible without a running TMOS instance. Gain remote system console access to the BMC and AOM functions through the same IP address of the TMOS management port, eliminating the need for a special or separate network. BIG-IP iSeries appliances also can show system information, such as sensor values for troubleshooting, on their color touchscreen LCD displays.
FIPS compliance at scale
The Federal Information Processing Standards (FIPS) specify requirements for cryptographic modules. FIPS compliance is required for many government agencies and industries such as financial services and healthcare that demand the highest standards in information, application, and data security. F5 offers a broad range of FIPS-validated hardware appliances that support FIPS 140-2 Level 2 and FIPS 140-3 Level 2 implementations for RSA cryptographic key generation, use, and protection when running validated versions of BIG-IP TMOS.
For additional protection, the F5 10350v-F/i7820-DF/i5820-DF ship with an embedded 3rd party FIPS-grade internal HSM (PCI card), validated by the Marvell company at FIPS 140-3 Level 3. F5 hardware FIPS appliances include integrated HSMs that have tamper-evident seals with a hardened-epoxy cover which, if removed, will render the card useless. The F5 BIG-IP system is not 140-2 Level 3 validated.
Specifications:
| Platform |
i2600 |
i2800 |
| Intelligent Traffic Processing |
L7 requests per second: 350K
L4 connections per second: 125K
L4 HTTP requests per second: 600K Maximum
L4 concurrent connections: 14M
Throughput: 10 Gbps L4/L7 |
L7 requests per second: 650K
L4 connections per second: 250K
L4 HTTP requests per second: 1M Maximum
L4 concurrent connections: 14M
Throughput: 10 Gbps L4/L7 |
| Hardware Offload SSL/TLS |
ECC† : 2.1K TPS (ECDSA P-256)
RSA: 2.5K TPS (2K Keys)
5 Gbps bulk encryption* |
ECC† : 3.5K TPS (ECDSA P-256)
RSA: 4.3K TPS (2K Keys)
8 Gbps bulk encryption* |
| FIPS SSL |
N/A |
N/A |
| Hardware Compression |
N/A |
5 Gbps |
| Hardware DDoS Protection |
N/A |
N/A |
| TurboFlex Performance Profiles |
N/A |
Tier 1 |
| Software Compression |
3 Gbps |
N/A |
| Software Architecture |
64-bit TMOS |
64-bit TMOS |
| On-Demand Upgradable |
Yes |
N/A |
| Virtualization (Maximum Number of vCMP Guests) |
N/A |
N/A |
| Processor |
One 2-Core Intel Pentium processor (total 4 hyperthreaded logical processor cores) |
One 2-Core Intel Pentium processor (total 4 hyperthreaded logical processor cores) |
| Memory |
16 GB DDR4 |
16 GB DDR4 |
| Hard Drive |
1x 500 GB Enterprise Class HDD |
1x 500 GB Enterprise Class HDD |
| Gigabit Ethernet CU Ports |
Optional SFP |
Optional SFP |
| Gigabit Fiber Ports (SFP) |
4 SX or LX (sold separately) |
4 SX or LX (sold separately) |
| 10 Gigabit Fiber Ports (SFP+) |
2 SR/LR (sold separately);
Optional 10G copper direct attach |
2 SR/LR (sold separately);
Optional 10G copper direct attach |
| 40 Gigabit Fiber Ports (QSFP+) |
N/A |
N/A |
| Power Supply |
1x 250W Platinum AC PSU (Additional PSU optional,
2x 650W DC PSU Option) |
1x 250W Platinum AC PSU (Additional PSU optional,
2x 650W DC PSU Option) |
| Typical Consumption |
95W (single power supply, 110V input)** |
95W (single power supply, 110V input)** |
| Input Voltage |
100–240 VAC +/- 10% auto switching, 50/60hz |
100–240 VAC +/- 10% auto switching, 50/60hz |
| Typical Heat Output |
325 BTU/hour (single power supply, 110V input)** |
325 BTU/hour (single power supply, 110V input)** |
| Dimensions |
1.72” (4.37 cm) H x 17.4” (44.2 cm) W x 22.5” (57.15 cm) D
1U industry standard rack-mount chassis |
| Weight |
20 lbs. (9.07 kg) (single power supply) |
| Operating Temperature |
32°F to 104°F |
| Operational Relative Humidity |
5% to 85% at 40º C |
| Safety Agency Approval |
ANSI/UL 60950-1-2014
CSA 60950-1-07, including A1:2011+A2:2014
IEC 60950-1:2005, A1:2009+A2:2013
EN 60950-1:2006+A11:2009+A1:2010+A12:2011+A2:2013 |
| Certifications/ Susceptibility Standards |
ETSI EN 300 386 V1.6.1 (2012)
EN 55032:2012 Class A: EN 61000-3-2:2014
EN 61000-3-3:2013: EN 55024:2010
FCC Class A (Part 15), IC Class A, VCCI Class A |
Notes: Performance-related numbers are based on local traffic management services only. Only optics provided by F5 are supported.
* Maximum throughput.
** Please refer to the Platform Guide: i2000 Series for the latest power ratings for your specific configurations (SSL, SSD, highline input voltage, DC, etc.).
† ECDHE-ECDSA-AES128-SHA256 cipher string tested.