Overview:
F5 BIG-IQ Centralized Management provides a central point of control for F5 physical and virtual devices and for the solutions that run on them. It simplifies management, helps ensure compliance, and gives you the tools you need to deliver your applications securely and effectively.
BIG-IQ manages policies, licenses, SSL certificates, images, and configurations for F5 devices and for the following F5 modules:
- BIG-IP Local Traffic Manager (LTM)
- BIG-IP Application Security Manager (ASM)
- BIG-IP Advanced Firewall Manager (AFM)
- BIG-IP Access Policy Manager (APM)
- F5 Secure Web Gateway Services
- BIG-IP DNS
- F5 WebSafe and F5 MobileSafe (monitoring only)
BIG-IQ supports BIG-IP, VIPRION, and the new F5 iSeries hardware platforms—as well as BIG-IP virtual editions (VEs) and Per-App VEs, whether they are running locally or in the cloud. It is ideal for organizations that require central management of F5 devices and modules, license management of BIG-IP VEs, or central reporting and alerting on application availability, performance, and security.
BIG-IQ now features “Application Centric Management,” which includes the following:
- A service catalog of application templates for BIG-IP LTM configurations so that you can quickly and easily roll out new applications or replicate existing ones.
- Fine-grained Roles-Based Access Control (RBAC), which allows management selfservice of application services.
- Support for the “Per Application” ADC model, including full management of Per-App VEs.
Manage in the Cloud
BIG-IQ Centralized Management saves you time and money by providing a single point of management of all your BIG-IP devices—whether they are on premises, or in a private or public cloud. BIG-IQ can manage any physical or virtual BIG-IP device so long as it can establish layer 3 connectivity for management by UI or through the APIs.
BIG-IQ supports BIG-IP products in both private and public clouds, helping you ensure consistent networking and security policies no matter where your applications reside. BIG-IQ can run on AWS and in most private cloud architectures. Consult an F5 representative about support for Microsoft Azure, Google Cloud Platform, and other public cloud systems.
Fine-Grained Management with Roles-Based Access Control
BIG-IQ 5.4 and above supports fine-grained RBAC, allowing security and application teams to manage their own applications without depending on network administrators. Use BIG-IQ’s predefined roles or create your own to manage who can see, edit, and deploy dashboards and policies for application delivery and security. Roles can be associated with local users and groups or users and groups from remote RADIUS or LDAP servers.
Central Logging, Reporting, and Auditing
BIG-IQ Centralized Management is a single solution for logging, reporting on, and auditing your F5 devices. Logs can be collected by BIG-IQ’s Data Collection Devices (formerly called “Logging Nodes”).
Data Collection Devices collect statistics and/or events from BIG-IP devices, and create dashboards and reports to track the health of your application services. Licenses are available free of charge. Speak to your F5 sales representative for details.
Manage:
Manage BIG-IP Devices
Use BIG-IQ Centralized Management to manage physical and virtual BIG-IP devices, including administration workflows such as discovery and inventory, F5 TMOS operating system upgrades, configuration file and license management, and monitoring.
BIG-IQ offers both an innovative, workflow-based user interface for customers looking for an out-of-the-box central management solution, and a comprehensive set of RESTful APIs for those who want to integrate Application Delivery Controller (ADC) management into other network management solutions.
Device management with BIG-IQ saves time and money by simplifying the often-complex task of configuring and updating ADCs. Just as important, BIG-IQ increases IT agility, allowing the network to adapt automatically by seamlessly integrating deployment, configuration, and licensing of BIG-IP VEs.
Device management—key uses
- Inventory and track up to 600 devices and device health.
- Manage licensing of up to 5,000 devices.
- Back up, restore, and upgrade BIG-IP device images and configurations.
- View iHealth reports for BIG-IP devices
- Evaluate and deploy full or partial configurations on all modules except BIG-IP APM.
- Deploy, renew, or change SSL certificates. Receive timely alerts before certificates expire.
Advantages of BIG-IP device management
- Device discovery and monitoring: Discover, track, and monitor BIG-IP devices—whether physical or virtual—including key metrics such as CPU/memory, disk usage, and high availability status.
- Centralized software upgrades: Centrally manage BIG-IP upgrades (from TMOS versions 10.2.0 and above) by uploading TMOS releases into BIG-IQ Centralized Management and directing the upgrade process for managed BIG-IP devices from one place.
- License management: Centrally manage BIG-IP VE licenses, granting and revoking licenses as business needs change. Gain the flexibility to license devices only as needed, maximizing the return on your BIG-IP investment. Assign different license pools to different applications or tenants for more flexible provisioning. As of version 5.4, BIG-IQ supports license management in OpenStack-based environments.
- Utility and subscription license usage reporting: Enable subscription and utility licensing of BIG-IP and Per-App VE devices by generating and delivering reports of device usage over time.
- Configuration, backup, and restore: Use BIG-IQ as a central repository of BIG-IP configuration files (UCS). Back up and restore system information on demand or as a scheduled process.
- BIG-IP device cluster support: Monitor high availability (HA) and clusters for BIG-IP devices.
- BIG-IP iHealth integration: Receive easy access to detailed reports on the health of BIG-IP devices.
- Evaluate and deploy all or a subset of configuration changes: These include changes that have been staged, allowing for more control over what changes are deployed at what time (includes all modules except BIG-IP APM).
- Password management: Update passwords on individual or groups of BIG-IP devices.
- SSL management: Deploy, renew, or change SSL certificates and Certificate Revocation Lists (CRLs). Receive timely alerts before certificates expire.
- Fine-Grained RBAC: Allows administrators to define roles and assign fine-grained control over configuration objects and tasks to those roles.
- Remote script management: Deploy and execute scripts on remote BIG-IP devices.
Manage BIG-IP APM and Secure Web Gateway Services
BIG-IQ offers central management of BIG-IP Access Policy Manager and F5 Secure Web Gateway Services devices. BIG-IP APM is a high-performance access and security solution that provides unified global access to your applications, network, and cloud. BIG-IP APM converges and consolidates remote, mobile, LAN, and web access—as well as wireless connectivity—within a single management interface.
Some organizations face the challenge of efficiently managing multiple BIG-IP APM devices. BIG-IQ handles up to 100 BIG-IP APM and Secure Web Gateway Services appliances, enabling you to view and manage devices and policies from a “single pane of glass.”
BIG-IP APM and Secure Web Gateway Services management— key uses
- Understand and control access security (VPN, SSO, federation) access policies with the Visual Policy Editor.
- Stage and push policies to selected BIG-IP APM devices.
- Achieve centralized, secure access management anytime, from anywhere.
- Ensure access policy compliance across the enterprise.
- Push out policy updates and revisions from a central location.
- Gain extensive reporting on your SSL VPN, VDI, users, web access application usage, and Secure Web Gateway Services activity.
Advantages with BIG-IP APM and Secure Web Gateway Services
- Import and edit policies. Push out policy updates and revisions from a central location.
- View and edit policies with the BIG-IP APM Visual Policy Editor (VPE).
- Configure and deploy VPN policies consistently from BIG-IQ across your geographically distributed BIG-IP APM devices.
- Edit location-specific objects (LSOs).
- Utilize web and cloud (federated) applications usage monitoring dashboards and drilldown views.
- Troubleshoot authentication failures and denied sessions using the new troubleshooting dashboards.
- Track remote access (VMware and Citrix VDI) environment usage and review granular consumption details for each VDI application.
- Search for individual users to view all activity or kill sessions directly from BIG-IQ across all BIG-IP devices.
- View reports on any combination of discovered BIG-IP devices, access groups, and clusters.
- View graphs for typical areas of concern and interest, such as logins across crossgeographical comparisons and Secure Web Gateway Services usage.
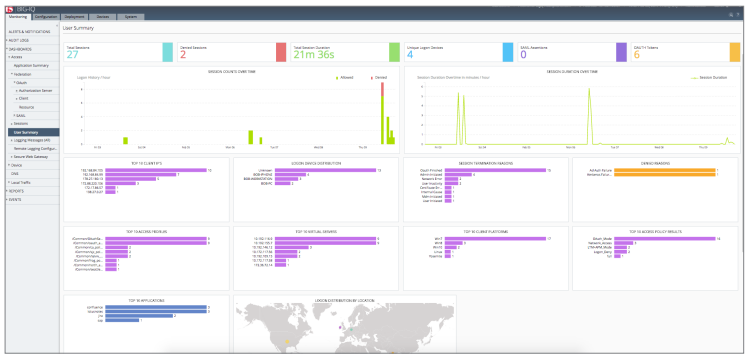
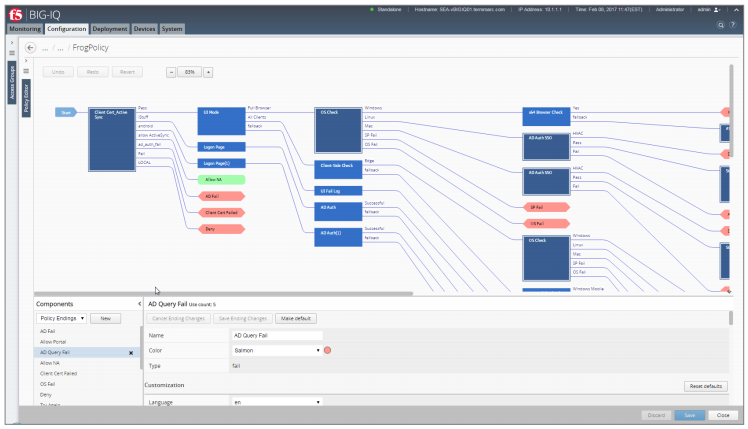
BIG-IQ provides flexible dashboards and the powerful Visual Policy Editor to help manage network access policies and events.
Manage F5 Security Solutions
BIG-IQ Centralized Management provides policy deployment, administration, and management for mid-sized and large organizations securing their applications and their networks with BIG-IP Application Security Manager and BIG-IP Advanced Firewall Manager.
Security management—key uses
- Web application security with BIG-IP ASM
- Ensure consistent security policies wherever applications reside.
- Share, edit, monitor, and evaluate configurations, profiles, and policies.
- Manage and distribute signatures.
- Export policies.
- Get central security reports and alerts.
- Use Central Policy Builder to create and distribute policies to BIG-IP devices (requires use of TMOS 13.1).
- Network security with BIG-IP AFM
- Discover and monitor devices and firewalls.
- Manage shared objects (address lists, port lists, rule lists, policies, and schedules).
- Manage L3–4 firewall policies.
- View firewall audit logs.
- Deploy configurations from snapshots and preview differences between snapshots.
- Enable multi-user editing through a locking mechanism.
- Get security reports and alerts.
- Complete IP Intelligence configuration management.
Advantages of reporting
Reporting for BIG-IP AFM includes network firewall, DDoS, and IP Intelligence reports from individual or groups of BIG-IP devices. BIG-IQ also creates firewall rule reports.
Reporting for BIG-IP ASM includes:
- Application: Get information about requests based on application services templates (F5 iApps), virtual servers, security policies, attack types, violations, URLs, client IP addresses, IP address intelligence (reputation), client countries, severities, response codes, request types, methods, protocols, viruses detected, usernames, and session identification numbers.
- Anomalies: Access graphs, charts, and statistical information about anomaly attacks, such as brute force attacks and web scraping attacks. Use these charts to evaluate traffic to web applications and security policy vulnerabilities.
- DDoS: View charts and reports that show information about DDoS attacks and mitigations in place on the system.
Manage BIG-IP LTM
BIG-IQ Centralized Management increases your productivity and allows you to deliver applications more effectively. It also serves as a unified management solution for BIG-IP Local Traffic Manager modules.
BIG-IQ handles many ADC functions including configuration management, health monitoring, certificate management, and large-scale configuration templating.
BIG-IP LTM management— key uses
- See the configuration of all your BIG-IP LTM devices.
- Manage key load balancing attributes such as VIPs, pools, members, profiles, and nodes.
- Create, view, edit, and apply iRules.
- Monitor state and availability for BIG-IP LTM objects.
- Provide application owners with self-service control (enable, disable, force offline) of virtual servers and pool members.
Advantages with BIG-IP LTM
- Import and view devices and their health as well as the state and availability of all BIG-IP LTM objects.
- Evaluate, stage, and deploy partial and complete configurations.
- Create a catalog of application templates to allow customers to rapidly deploy similar applications.
- Create configuration snapshots.
- Create, discover, edit, remove, and import SSL traffic certificates.
- View and alert on expiration of SSL traffic certificates.
- Create, discover, edit, remove, or clone virtual servers.
- Create, discover, edit, and remove F5 iRules (F5’s scripting language), nodes, pools, SNAT pools, and pool members.
- Copy any monitor and most profiles from a source BIG-IP LTM and deploy to other BIG-IP LTMs managed by BIG-IQ. Evaluate, stage, and deploy partial and complete configurations.
- Get statistics monitoring for BIG-IP LTM objects (virtual server, pools, pool members, nodes, iRules).
- View and search for relationships between BIG-IP LTM objects.
DNS Visibility
BIG-IQ Centralized Management offers BIG-IP DNS sync group support. Using the tools available on the BIG-IP user interface, it can be difficult to determine the health of your DNS sync groups. When you use BIG-IQ to manage your DNS sync groups, the task becomes quite straightforward. Conduct a quick health check and diagnose health issues. You can also set up an alert to notify you if a sync group health issue occurs, if certificates are out of date, or if services are not running.
BIG-IP DNS visibility—key uses
- Track and manage devices running BIG-IP DNS.
- Back up and restore devices.
- Troubleshoot DNS sync group health.
- View DNS statistics and status.
- Centrally configure BIG-IP DNS security services.
Advantages of DNS visibility
- Add BIG-IP DNS and BIG-IP LTM devices to existing sync groups.
- Analyze F5 iQuery connection information to help identify DNS sync-group issues.
- View high-level statistics across your DNS infrastructure showing status of DNS sync groups and devices.
- View both real-time and historical DNS statistics.
- View configuration of DNS devices.
Statistics and Visibility with BIG-IQ Centralized Management:
BIG-IQ Centralized Management provides extensive visibility into the health and performance of your BIG-IP devices. It starts where F5’s Application Visibility and Reporting (AVR) leaves off, collecting and aggregating statistics from your BIG-IP devices both locally and in the cloud.
With BIG-IQ, it’s easy to identify and troubleshoot application performance and delivery issues. It provides flexible dashboards showing key metrics in security, network access, and BIG-IP health and performance.
BIG-IQ collects and aggregates detailed metrics such as transactions per second, server and client latency, request and response throughput, and sessions. You can view metrics for virtual servers, pool members—and in the case of BIG-IP APM monitoring— URLs, applications, locations, and additional statistics about application traffic running through the BIG-IP system. It also uses the data collected to produce easy to use dashboards and reports.
Categories of data collected for dashboards include:
- Device health and performance metrics
- Local traffic (virtual server and pool traffic as well as iRules metrics)
- DNS traffic and performance
Statistics and dashboards— key uses
- Use dashboards to quickly track the health and performance of your BIG-IP devices.
- Quickly identify virtual servers or pools with performance issues.
- Track the performance of your DNS infrastructure.
Data Collection Devices
BIG-IQ provisions Data Collection Devices to manage and store alerts or events from one or more BIG-IP systems. Speak to your F5 sales representative for more information about obtaining and provisioning Data Collection Devices.
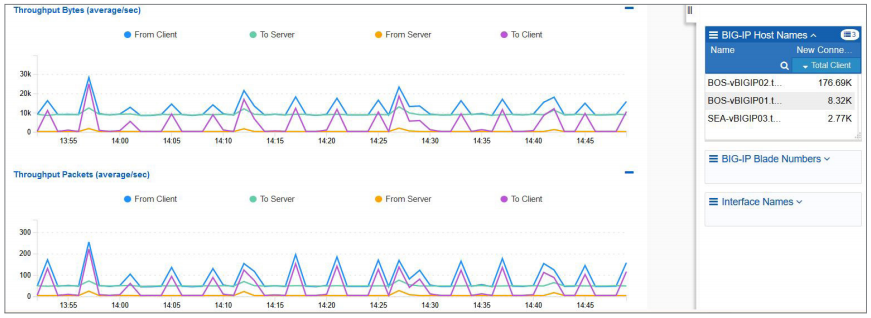
BIG-IQ Centralized Management provides flexible dashboards showing key performance metrics.
BIG-IQ Centralized Management 7000 Platform:
BIG-IQ Centralized Management is available as a virtual edition or on an enterprise-grade appliance. Providing single vendor accountability and consistent F5 hardware for managing your F5 devices in non-virtualized environments, the BIG-IQ 7000 platform provides the quality and reliability of purpose-built F5 hardware platforms.
| BIG-IQ Centralized Management 7000 Platform |
| L7 requests per second |
800K |
| L4 connections per second |
390K |
| L4 HTTP requests per second |
3.5M
|
| Throughput |
40 Gbps/20 Gbps L4/L7 |
| Software Architecture |
64-bit TMOS |
| On-Demand Upgradable |
Yes |
| Processor |
1 quad core Intel Xeon processor (total 8 processing cores) |
| Memory |
32 GB |
| Hard Drive |
Two 1 TB (RAID 1) |
| Gigabit Ethernet CU Ports |
4 |
| Gigabit Fiber Ports (SFP) |
Optional SFP |
| 10 Gigabit Fiber Ports (SFP+) |
8 SR or LR (sold separately, 2 SR included) |
| 40 Gigabit Fiber Ports (QSFP+) |
N/A |
| Power Supply |
Two 400W included (80 Plus Gold Efficiency), DC optional |
| Typical Consumption |
205W (dual supply, 110V input) |
| Input Voltage |
90–240 VAC, 50/60hz |
| Typical Heat Output |
700 BTU/hour (dual supply, 110V input) |
| Dimensions |
3.45" (8.76 cm) H x 17.3" (43.94 cm) W x 21.4" (54.36 cm) D
2U industry standard rack-mount chassis |
| Weight |
40 lbs. (18.14 kg) (dual power supply) |
| Operating Temperature |
32° to 104° F (0° to 40° C) |
| Operational Relative Humidity |
10 to 90% @ 40° C |
| Safety Agency Approval |
ANSI/UL 60950-1-2011 CSA 60950-1-07, including
Amendment 1:2011 Low Voltage Directive 2006/95/EC
CB Scheme, EN 60950-1:2006+A11:2009+A1:2010
+A12:2011, IEC 60950-1:2005, A1:2009 |
| Certifications/ Susceptibility Standards |
EN 300 386 V1.5.1 (2010-10);
EN 55022:2010;
EN 61000-3-2:2006+A1:2009+A2:2009;
EN 61000- 3-3:2008;
EN 55024:2010;
EN 55022:2010;
EN 61000-3- 3:2008;
EN 55024:2010;
USA FCC Class A |





